Analysis of Image Reconstruction Schemes Based on Self-Embedding and Digital Watermarking
Abstract
This dissertation deals with digital image authentication and reconstruction techniques based on fragile digital watermarking. The main focus of the presented analysis addresses the achievable reconstruction performance, the inherent restoration trade-offs, and the applicable operation bounds. The analysis is based on a new theoretical model of the self-embedding problem, and ultimately leads to the development of an efficient self-embedding scheme, capable of high-quality reconstruction even under extensive tampering. For a benchmark configuration of the proposed scheme, an average peak signal to noise ratio for 10,000 natural images is 37 dB, even when up to 50% of the image area becomes tampered.
The content reconstruction problem is modeled as an erasure communication channel, and implemented in practice with the use of digital fountain codes. With proper design of the self-embedding scheme, it is possible to exploit the remaining authentic image content, and overcome the limits of traditional erasure communication. It becomes possible to use reference streams significantly longer than the available embedding capacity.
The presented analysis is first performed for the case of uniform-fidelity reconstruction, and then extended to the case of adaptive self-embedding. The latter is an emerging research direction, which is of high importance in certain applications, e.g., in the authentication of closed circuit television footage. By controlling the reconstruction quality for each image block individually, a new degree of freedom is introduced. With such flexibility it becomes possible to bias the process towards better image quality, or better robustness against content modifications. In order to calculate the mapping between the image blocks and the reconstruction quality, a dedicated algorithm is proposed, which allows for providing guarantees on the quality of individual image fragments, and the achievable tampering rates.
The dissertation also discusses reconstruction quality optimization techniques. The commonly used uniform quantization procedure is replaced with optimal Lloyd-Max code-books, and the allocation of the reference payload is performed in a formalized framework. Such an optimized self-embedding scheme is experimentally compared to 5 state-of-the-art alternative schemes in a common evaluation scenario.
All of the presented theoretical results are supported by exhaustive experimental evaluation. The obtained results lead to important insights on the design of efficient self-embedding schemes. For the sake of research reproducibility, the relevant Matlab code can be obtained online.
Supplementary Materials
The goal of this package is to provide a means to reproduce the results presented in my dissertation. By no means should this implementation be regarded as fit for practical deployments. Certain aspects of the working self-embedding scheme use simplified mechanisms, sufficient only to demonstrate the proposed concepts.
If you find this code useful in your research please cite the appropriate publications:
- P. Korus and A. Dziech, Efficient Method for Content Reconstruction with Self-Embedding, IEEE Tran. Image Proc., 2013
- P. Korus and A Dziech, Adaptive Self-Embedding Scheme with Controlled Reconstruction Performance, IEEE Tran. Inf. Forensics and Security, 2014
The package contains:
- Matlab scripts for reproducing the most important results from my dissertation.
- Supplementary results, including obtained images, charts, etc.
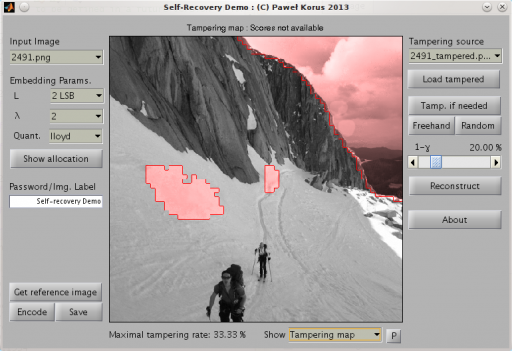
- Interactive demonstration of the developed reference scheme.
The code has been tested with Matlab 2011b and 2012a on Debian Linux. Selected routines are implemented as MEX routines, and binaries for both 32-bit and 64-bit distributions are provided. A slower m-file version of the routines is available, and the scripts should fallback to using them when necessary.
License
Copyright (c) 2013, Paweł Korus. All rights reserved.
The author is with the Department of Telecommunications of AGH Universityof Science and Technology, Kraków, Poland.
Permission to use, copy, or modify this software and its documentation for educational and research purposes only and without fee is hereby granted, provided that this copyright notice and the original authors' names appear on all copies and supporting documentation. This program shall not be used, rewritten, or adapted as the basis of a commercial software or hardware product without first obtaining permission of the authors. The authors make no representations about the suitability of this software for any purpose. It is provided "as is" without express or implied warranty.
Neither the name of the author not the AGH University of Science and Technology may be used to endorse or promote products derived from this software without specific prior written permission.